Access control systems are all about keeping people out of places they don’t belong.
You know who needs access to business-critical areas around your facility, but applying the right identification technology methods to your premises can be a challenge.
In this post, we’ll examine the three main access control methods and how they work together to create a layered business security system.
What is Access Control?
Access control means controlling who has access to certain areas of your property by using automated technology. People can verify their identity by swiping a card (what you have), entering a code or password (what you know), or through biometrics like a fingerprint (who you are).
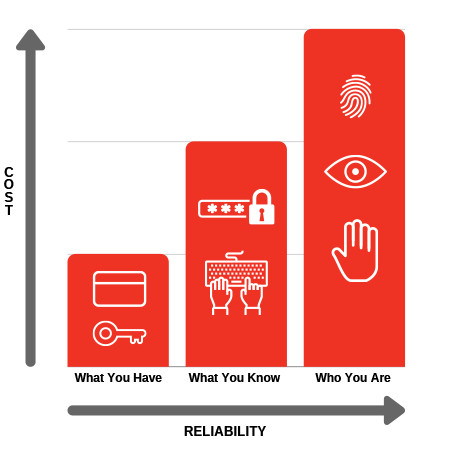
Keep in mind that these identification methods all have differing levels of reliability and associated costs. Even if money were no object, it wouldn’t be wise to blanket your whole facility with the highest security technology. Strategically using each method in your security system will keep costs down and make it user-friendly.
What Needs Protection?
The first step in creating a strong controlled access system is mapping out your facility. You need to identify all areas and entry points that need different levels of security.
This can be as simple as sketching your property on scratch paper to help get a comprehensive view of where potential threats could enter your facility.
Quick note: Physical security can also mean protection from disasters (fires, floods, tornadoes) or utility malfunctions (power loss, HVAC failure). In this article, we’re focused on protection from on-site human intrusion.
Mapping out your facility will help build a layered security system that is cost-effective, non-intrusive and more secure. You’ll have a better understanding of which areas need protection with more reliable and expensive technologies.
Naturally, you’ll implement what is called depth of security. With depth of security, access methods become increasingly stringent as you progress to the most business-sensitive areas.
For example, entry to the grounds of an organization requires a card swipe -> entry to the building requires a code -> entry to the server room requires a password plus a biometric.
Combining ID methods increases the reliability at that point. In the example below, the server room is secured by its own door access control system, plus the systems of the outer entry points that must be accessed first.
Depth of Security Infographic
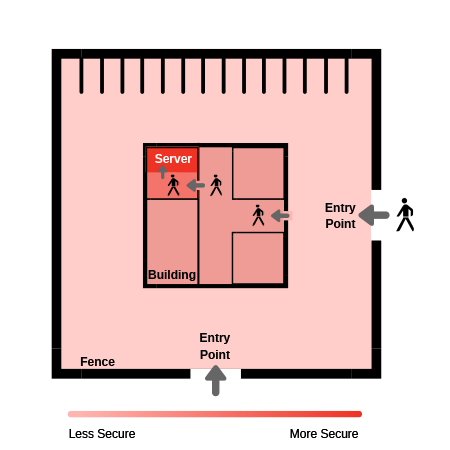
What You Have
The ‘what you have’ method can be something you wear or carry with you to identify yourself. This can be a key, swipe card, or a FOB on your key chain.
For example, if you have a membership to a 24/7 fitness center you probably have something on your keyring to swipe to get into the gym after hours.
This method is the least reliable when talking about security because there’s no guarantee the access token is being used by the right person. Physical tokens are easily shared, stolen or lost and used by someone else.
What You Know
The ‘what you know’ method is more reliable and secure than using a physical token to gain access to an area. The most common examples of this method are passwords and codes.
If your organization has a password policy this method can be effective and help with the password dilemma many people face:
Passwords/Codes that are easy to remember are usually easy to guess; Passwords/Codes that are hard to remember are likely to be written down which makes them liable to be stolen.
Who You Are
The ‘who you are’ method gives access to areas by recognizing human features like fingerprints, eyes, faces or voices. This is called biometrics and it offers the most reliable access control, but is also the most expensive to implement.
Biometrics is most likely implemented on the innermost layer of your security system alongside another method of identification such as a pin code. Biometrics are usually very reliable systems.
The most common source of unreliability with this method is failure to recognize an individual (false rejection), not spoofing by an imposter.
Identification Methods: Reliability vs. Cost
Building a Commercial Security Access Control System
Implementing the right controlled access system for your organization strategically balances the risks of the wrong people having access to business-critical areas against the system costs and nuisance factors of your security measures.
Designing a security system is a complicated art. That’s why we recommend you work with an access control company that knows how to layer access control security technologies to give you the most protection.
In short, you know who needs access to what areas; we know how to make it happen.
Key points to consider when planning your access control system:
Type of Equipment
It wouldn’t be beneficial to install biometric access control at every entry point. This would be highly inconvenient and likely expensive. Think about which identification methods are appropriate for each access-controlled area to develop a layered system (remember the depth of security strategy).
Combining Identification Methods
Using a combination of ID methods to secure your facility will also help control costs and build up your layered approach to security. Think about how you could use the lower-cost methods like what you have on the outer perimeter of your property and incorporate more expensive biometrics on the innermost levels of your system.
User Acceptance
When planning your system your focus is on securing your assets. It’s also important to take into account how user-friendly the system is for people. You wouldn’t want to spend time and money on a system that becomes a source of frustration for people.
Integration with Other Equipment
Combining access control with cloud-based video surveillance will give you maximum visibility of your facility. You’ll have secure remote access to cameras and access control equipment from anywhere. You’ll know exactly who entered what area and at what time.
Your People: The Weakest Link & The Strongest Backup
The people working at your organization can be your biggest threat and your best line of defense. At the end of the day, your organization and its technology are run by people. Security technology has come a long way in the last 20 years but having a well-trained person as a last line of defense is still valuable.
On the other hand, humans aren’t without flaws. Criminals have also become more innovative in their tactics. Creative social engineering techniques can take advantage of unaware and untrained employees.
Educating your end-users will help them recognize hacking attempts and mitigate the risk of a breach.
Adding access control to your organization’s security system helps you find a balance between protection and cost. A well-constructed plan is key to building depth of security for your facility and will help create multiple layers of security.
Protecting business-critical assets with a physical security system is just as important as network security. You’ll minimize the risk of someone damaging equipment or launching a software attack on an unsecured computer.
Once you understand what your organization needs and mapped areas around the facility that need to be secured, working with security experts makes implementation even easier. Our physical security engineers will work to develop a security solution that fits your budget and protects your organization.
No matter where your business security system is hosted, in the cloud, on-premise or as a hybrid of both, Loffler can help build a system that meets your business’ unique needs.
Read Next: 4 Commercial Intrusion Alarm System Benefits
Reference: Niles, S. (n.d.). Physical Security in Mission Critical Facilities [PDF]. Schneider Electric’s Data Center Science Center.

Anthony is the Practice Manager of Physical Security at Loffler Companies. He began his technology career in 1993 installing POS and audio/video equipment in retail and commercial environments. With more than 25 years of technology background, Anthony has built and managed several enterprise-level surveillance systems consisting of more than 56,000 cameras in 830 locations in the United States and Canada. He was instrumental in the design and implementation of major surveillance systems for Life Time Fitness – supporting 9000+ cameras running Milestone Systems and JCPenney – supporting 42,000+ cameras running ExacqVision. In addition, he brings a strong background in operational leadership and knowledge in multi-site real estate management and construction. Anthony has had certifications with AXIS, Milestone, Genetec, ASIS, BICSI, NICET, Microsoft and Cisco along with various Access Control, Audio Visual and Project Management certifications. In his free time, he enjoys the outdoors with his son and daughter.




